What is Encryption and How Does it Work?
April 17, 2024
Encryption is the process of encoding information in such a way that only authorized parties can access it.
It's a fundamental aspect of modern cybersecurity and privacy protection.There are several encryption techniques and algorithms, ranging from symmetric encryption, where the same key is used for both encryption and decryption, to asymmetric encryption,
which uses a pair of keys: a public key for encryption and a private key for decryption.Now to understand more about encryption we need to know about
In the context of cryptography, a "key" refers to a piece of information used to control the cryptographic operations of encryption and decryption.
Keys play a crucial role in ensuring the security and confidentiality of data in cryptographic systems.So now diving into the topic, basically there are 2 types of encryption techniques as I have already mentioned, symmetric and asymmetric.
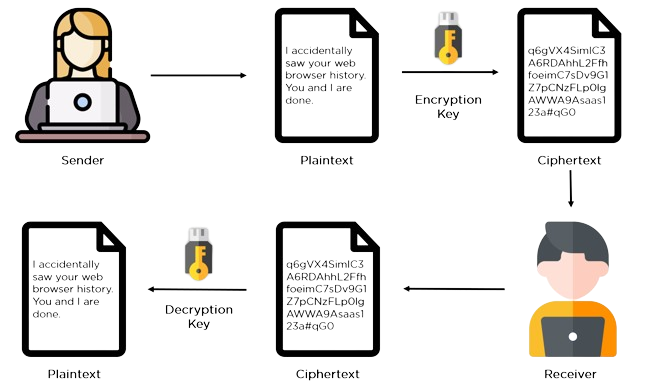
Talking about Symmetric Encryption Technique, also known as secret-key or private-key cryptography, involves using a single key for both encryption and decryption of data. Unlike asymmetric cryptography, where separate keys are used for encryption and decryption, symmetric cryptography uses the same secret key for both operations.
Here's how it works:
- Key Generation: In symmetric cryptography, a secret key is generated by the communicating parties or by a trusted third party. This key must be kept confidential between the sender and the receiver to ensure the security of the communication.
- Encryption: To encrypt a message or data, the sender applies the secret key to transform the plaintext into ciphertext. This process scrambles the original message in such a way that it becomes unintelligible to anyone who does not possess the secret key.
- Decryption: The recipient, who also possesses the secret key, uses the same key to decrypt the ciphertext back into plaintext. By applying the key in reverse, the recipient can recover the original message and understand its contents.
Also here are some key points of symmetric cryptography:
- Efficiency: Symmetric cryptography is typically faster and more efficient than asymmetric cryptography because it requires less computational overhead. Since only one key is involved, the encryption and decryption processes are simpler and quicker.
- security: The security of symmetric cryptography relies heavily on the confidentiality of the secret key. If an attacker gains access to the key, they can decrypt all communications encrypted with that key. Therefore, securely managing and distributing keys is crucial in symmetric cryptography.
- Key distribution: One of the primary challenges of symmetric cryptography is securely distributing the secret key to all parties involved in the communication. Since the same key is used for encryption and decryption, all parties must possess the key in advance to communicate securely.
Despite its efficiency and widespread use, symmetric cryptography faces challenges in key distribution and key management, especially in large-scale or distributed systems. However, when implemented and managed correctly, symmetric cryptography provides robust security for protecting sensitive information and securing communication channels.
So, its a lot about symmetric encryption now lets take a moment to know what is asymmetric encryption and how does it function?
Asymmetric encryption, also known as public-key cryptography, is a cryptographic system that uses a pair of keys for secure communication: a public key and a private key.
Unlike symmetric encryption, where the same key is used for both encryption and decryption, asymmetric encryption uses separate keys for these operations. Here's how asymmetric encryption works:
-
Key Generation:
Public Key: A public key is generated by a user and is freely distributed to anyone who wants to communicate securely with that user. The public key is used to encrypt messages intended for the owner of the key.
Private Key: A private key is generated along with the public key and is kept secret by the owner. The private key is used to decrypt messages that have been encrypted with the corresponding public key. - Encryption: To send a secure message to a recipient, the sender obtains the recipient's public key and uses it to encrypt the message. Once encrypted, the message can only be decrypted by the recipient using their private key.
- Decryption When the recipient receives the encrypted message, they use their private key to decrypt it and recover the original plaintext message. Since the private key is kept secret, only the recipient can decrypt the message.
The conclusion on encryption is multifaceted.
Security and Privacy: Encryption plays a crucial role in securing data, communications, and transactions. It's a fundamental tool for safeguarding sensitive information from unauthorized access or interception. Without encryption, sensitive data would be vulnerable to exploitation by cybercriminals, governments, or other malicious actors.
Legal and Ethical Considerations: While encryption enhances privacy and security, it also raises legal and ethical debates. Law enforcement agencies often advocate for backdoor access to encrypted communications for crime prevention and investigation purposes. However, such backdoors could weaken overall security and privacy, creating potential risks for individuals and businesses.
Balancing Act: Finding a balance between security and accessibility is essential. While it's important to empower individuals with strong encryption to protect their privacy, it's also crucial to address legitimate concerns regarding law enforcement and national security. This balance requires collaboration between technology companies, policymakers, and civil society to develop solutions that prioritize both security and privacy.
Technological Advancements:Encryption techniques continue to evolve to keep pace with advancements in computing power and emerging security threats. Quantum computing, for example, presents both opportunities and challenges for encryption. While it could potentially break current encryption algorithms, it also offers new possibilities for developing quantum-resistant encryption methods.
Global Implications: Encryption policies and regulations vary across jurisdictions, leading to discrepancies in privacy protections and law enforcement capabilities. International cooperation and standardization efforts are necessary to ensure consistent and effective encryption practices globally.
In conclusion, encryption is indispensable for protecting privacy and security in the digital age. However, its implementation requires careful consideration of legal, ethical, and technological factors to strike the right balance between security, privacy, and accessibility.